[247 / 1 / ?]
https://kjzz.org/content/1719314/arizona-election-audit-confirms-bidens-win-maricopa-county-also-casts-doubts
>https://media.kjzz.org/s3fs-public/20210919_-_Maricopa_County_Forensic_Audit_-_Volume_I_-_Executive_Summary.pdf
Executive summary
>https://media.kjzz.org/s3fs-public/20210830_-_Maricopa_County_Forensic_Audit_-_Volume_II_-_Methodology_and_Operations.pdf
methodology
>https://media.kjzz.org/s3fs-public/20210919_-_Maricopa_County_Forensic_Audit_-_Volume_III_-_Results_Details_003.pdf
the good stuff, findings
Post your favorites.
dont be shy.
paste ballot tallying results.
paste findings.
past the "about cyber ninjas" section
go ahead and have fun. Ill start:
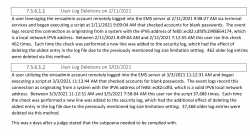
>A user leveraging the emsadmin account remotely logged into the EMS server at 2/11/2021 9:08:27 AM via terminal services and began executing a script at 2/11/2021 9:09:04 AM that checked accounts for blank passwords. The event logs record this connection as originating from a system with the IPV6 address of e80::ec82:cdfd%1998664174, which is a local network IPV6 address. Between 2/11/2021 8:09:04 AM and 2/12/2021 7:12:55 AM this user ran this check 462 times. Each time the check was performed a new line was added to the security log, which had the effect of deleting the oldest entry in the log file due to the previously mentioned log size limitation setting. 462 older log entries were deleted via this method.
>https://media.kjzz.org/s3fs-public/20210919_-_Maricopa_County_Forensic_Audit_-_Volume_I_-_Executive_Summary.pdf
Executive summary
>https://media.kjzz.org/s3fs-public/20210830_-_Maricopa_County_Forensic_Audit_-_Volume_II_-_Methodology_and_Operations.pdf
methodology
>https://media.kjzz.org/s3fs-public/20210919_-_Maricopa_County_Forensic_Audit_-_Volume_III_-_Results_Details_003.pdf
the good stuff, findings
Post your favorites.
dont be shy.
paste ballot tallying results.
paste findings.
past the "about cyber ninjas" section
go ahead and have fun. Ill start:
>A user leveraging the emsadmin account remotely logged into the EMS server at 2/11/2021 9:08:27 AM via terminal services and began executing a script at 2/11/2021 9:09:04 AM that checked accounts for blank passwords. The event logs record this connection as originating from a system with the IPV6 address of e80::ec82:cdfd%1998664174, which is a local network IPV6 address. Between 2/11/2021 8:09:04 AM and 2/12/2021 7:12:55 AM this user ran this check 462 times. Each time the check was performed a new line was added to the security log, which had the effect of deleting the oldest entry in the log file due to the previously mentioned log size limitation setting. 462 older log entries were deleted via this method.